E-Mail Security Phishing Attempts: How to determine if a fraudulent phishing attempt or ransomware is lurking in your Inbox
E-Mail Security Phishing
E-Mail Security is a daily concern for many companies, even with the correct firewalls, routers and layers of security in place. Ransomware attacks are increasing daily at an exponential level. According to the FBI, in 2016, an average of 4,000 ransomware attacks took place every day on businesses.Typically we would differentiate between the differences between phishing e-mails and ransomware distribution, yet after reading recent cyberthreat summaries, this has now changed. According to PhishMe Inc., the amount of phishing attempts containing a form of ransomware grew to 97.25% during Q3, up from 92% in Q1 2016. This is our new reality now.
Many of our clients contact us whenever an E-mail is in question, wanting to confirm the validity of an unexpected communication rather than suffering the costly and sometimes devastating effects of a ransomware or other e-Mail Security threats sitting in their inbox. We encourage this and will always answer preventive questions. Our team strives to educate users on how to help safely navigate around cyberthreats as often as possible. A study conducted at Friedrich-Alexander University in 2016 showed that 78% of people claim to be be aware of the risks of unknown links in emails , yet they click on the links anyway! Wow! We can do better than that! This pandemic E-Mail Security crisis is preventable and the following tips can certainly help squash the efforts of cybercriminals.
These fraudulent e-mails are gateways to technical devastation and Orange County Computer wants to help! We would like you to follow some basic rules to help guard yourself and others.
Rule #1 – Slow Down
Don’t multitask when reading your e-mails – Slow Down and look at each email in the preview window to determine if you should open the e-mail. Look at the subject line and ask your self, “Did my Bank of America account really get compromised?” or “Do I even have a Bank of America Account”?
Rule #2 – Assume that an unexpected e-mail is a phishing attempt until you look more closely at it.
Phishing attempts can look blatantly fake and some require a second look just to make sure. The common theme is phishing emails is surrounded by money and here are a few of the top phishing attempt subjects:
- Foreign Lottery Winner
- PayPal Account Deactivation
- Credit Card Account Compromised
- Bank Account Compromised
- Hijacked Profile
- Stranded Traveler, Urgent Request from a “Friend”
- Incoming Faxes
- Invoice Due
- CVS, Target, Walgreens, Walmart, Amazon Gift Cards
When handling these types of e-mails, simply opt to “BLOCK SENDER” and delete. You may also increase your spam settings to “HIGH” which will put many of these types of e-mails directly into your “JUNK” Box. Some legitimate e-mails may be placed in the “JUNK” folder, so just browse that folder every few days if you are looking for an item you haven’t received from someone.
Rule #3 – Verify Verify Verify
- Verify any and all sender information and check for the accuracy of spellings. Example: orders@amazons1.com vs. orders@amazon.com. UPS, Amazon, Paypal, Banks, etc., do not use varying website URLS. You can also search for amazons1.com and verify that the sender is fraudulent.
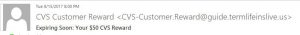
- If the sender has a name, look at the domain in which it comes from for example: an e-mail is sent and says its from “CVS Customer Reward” yet if you view the true e-mail address of the sender, it is coming from “CVS-Customer.Reward@guide.termlifeinslive.us” Obviously this is a fake e-mail as CVS e-mails would come from CVS and not Termlifeinslive.us.
3. If you receive an e-mail from someone in your contacts that you don’t think they would send you, contact that person and let them know about it. Most of the time, users have no idea that someone is cloaking their e-mail address and spamming people.
Rule #4 – Be Cautious of Attachments
- Do not open any e-mails with a .doc. .xls, .ppt attachment – This is one of the primary methods in which ransomware is spread. This is via Microsoft Office 2007 and 2003, which are unsupported by Microsoft and used by cybercriminals to spread the virus to unsuspecting users. Office programs with the attachments .docx, .xlsx, .pptx for Word, Excel and Powerpoint are acceptable, BUT always verify that you are waiting for an attachment from the sender before opening.
- If you receive an invoice email for an unpaid balance, check the sender’s authenticity and also verify that you work with the vendor in question” If you don’t know who the vendor is, or if the sender’s address is not 100% accurate, please do not open the e-mail.
Rule #5 – Upgrade Unsupported Operating Systems
If you are using a Windows XP or Windows Vista System, every time you use the Internet, you are just begging for a virus. These old Operating Systems are a cyber criminal’s dream. This is like leaving the front door to your house unlocked and broadcasting to everyone that you left town for a week. These old Operating Systems, no longer receive security updates to help block or detour viruses or hacks. Please, if you care about your data, personal information or credit rating, please immediately upgrade your system to a supported Operating System such as Windows 7, 8, 8.1 or Windows 10.
Rule #6 – Call Orange County Computer for Guidance
Every day we have clients contact us to verify real vs. fraudulent e-mails. We want to do our part to help eliminate these rampant E-Mail Security Threats. Give us a call at (949) 522-7709 and our staff will gladly answer your questions. We only ask that you do not send the email in question to us.
What Can You Do?
There are several things you can do to help in this situation. You have already helped by educating yourself and hopefully incorporating are helpful tools to protect yourself and others. There is one more thing you can do to help and that is to report these emails to the authorities which would be the FBI. To Report Suspicious emails, click here: The Department of Justice would like to hear from you. You may also report directly to the FBI Internet Crime Complaint Center (IC3) by clicking here: If you receive unsolicited e-mail offers or spam, you can additionally forward the messages to the Federal Trade Commission at spam@uce.gov.
We are happy to help. please call us at (949) 699-6619 with any questions.